
Ethical hacking step-by-step guide
Ethical hacking involves testing and securing systems by identifying vulnerabilities before malicious hackers can exploit them. Unlike cybercriminals, ethical hackers operate with permission and aim to improve security. They use the same techniques as their unethical counterparts but within legal and moral boundaries. This guide will walk you through the process of ethical hacking step-by-step, providing a structured approach to help you navigate the complex world of cybersecurity.
Introduction to Ethical Hacking
Ethical Hacking, also known as penetration testing or white-hat hacking, involves legally breaking into computers and devices to test an organization’s defenses. It is a crucial aspect of modern cybersecurity practices, helping organizations identify vulnerabilities in their systems and protect against malicious attacks.
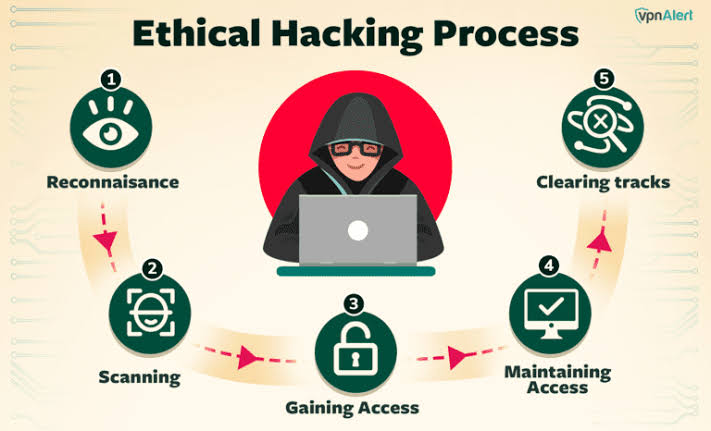
What is Ethical Hacking?
Ethical hacking, also known as penetration testing, involves simulating cyberattacks on systems to identify and address vulnerabilities before they can be exploited by malicious hackers. Unlike black hat hackers, ethical hackers work with permission and aim to strengthen security measures. Their goal is to find weaknesses in systems, applications, and networks to prevent potential breaches.
Importance of Ethical Hacking
In today’s digital landscape, organizations face numerous security threats. Ethical hacking is crucial because it helps identify and mitigate vulnerabilities, thus protecting sensitive data and maintaining the integrity of IT infrastructure. By proactively testing security measures, ethical hackers help prevent data breaches, financial losses, and reputational damage.
Getting Started with Ethical Hacking

Fundamental Skills Required
Networking Basics
Understanding networking fundamentals is essential for ethical hacking. Key concepts include IP addresses, subnetting, routing, and network protocols. Familiarity with TCP/IP, DNS, HTTP/HTTPS, and other networking protocols is crucial for identifying and exploiting vulnerabilities.
Operating Systems
Knowledge of various operating systems, including Windows, Linux, and macOS, is important. Ethical hackers must understand how different OSs handle security, manage user permissions, and respond to attacks. Linux, in particular, is widely used in the security community due to its versatility and open-source nature.
Programming and Scripting
Basic programming skills can significantly enhance your ethical hacking capabilities. Languages such as Python, Bash, and PowerShell are commonly used for writing scripts to automate tasks and develop exploits. Understanding code helps in analyzing software vulnerabilities and crafting exploits.
Essential Tools and Resources
Virtualization Software
To create a safe testing environment, use virtualization tools like VMware or VirtualBox. These tools allow you to run multiple operating systems on a single machine, enabling you to test different configurations and scenarios without affecting your primary system.
Security Tools
Equip yourself with essential security tools:
Nmap: For network scanning and discovery.
Wireshark: For network traffic analysis.
Metasploit: For exploitation and vulnerability testing.
Burp Suite: For web application security testing.
Setting Up a Learning Path
Begin with foundational courses and certifications, such as CompTIA Security+ or CEH (Certified Ethical Hacker). These will provide you with a structured learning path and essential knowledge to progress in ethical hacking.
Understanding Legal and Ethical Boundaries
Legal Frameworks
Understanding Laws and Regulations
Familiarize yourself with laws related to cybersecurity in your region. In the U.S., the Computer Fraud and Abuse Act (CFAA) governs unauthorized access. Internationally, regulations like GDPR (General Data Protection Regulation) and local laws affect how you handle data and conduct security tests.
Importance of Permission
Always obtain explicit written consent from system owners before conducting any tests. Unauthorized testing can lead to legal consequences and is considered unethical, regardless of your intentions.
